Content Distribution Networks (CDN) like Cloudflare have made internet fast all over the world. Cloudflare’s free tier is enough to make websites faster. It is easy to set up your domain which use content distribution networks for static content distribution. It allows users to set up applications, firewall, analytics, DNS, and page rules in addition to CDN. But this doesn’t come with downsides, if the CDN goes offline, your website goes down with it. Cloudflare has had technical problem which led to downtime throughout the world.
I decided to find a way to resolve the domain to their original IP. If you can find the original IP of the site’s host, you can receive content from the source bypassing the CDN. Our analysis show that this doesn’t work every time as domain fail to load with their host IP because of shared SSL certificates from Cloudflare.
There are few ways to find the host IP of the website. It includes checking the historic IP records or checking its sub-domains for possible IP leak. There may be other sophisticated methods out there that I do not know. Here I made a python scanner to check sub-domains.The code is made for personal research, however you are free to modify it.
The tool we are going to be using is CDNReveal. It scans through multiple subdomains from a list in attempt to find one that the website owner may have made exempt from CDN. Website administrators use subdomains to access web services like mail, control panel, and files. It exploits a choice of the domain user to let some sub-domains bypass the CDN.As a user sets up a domain with Cloudflare, it enumerates the domains’ sub domains. The user decides which DNS records should pass through Cloudflare. Users may choose to bypass the CDN for few sub-domains as domain names are easier to remember. Some of these sub-domains include mail, ftp, cPanel, and others.
The tool is a Python script and you can use the ‘-d’ argument for the domain. A typical command would look like:
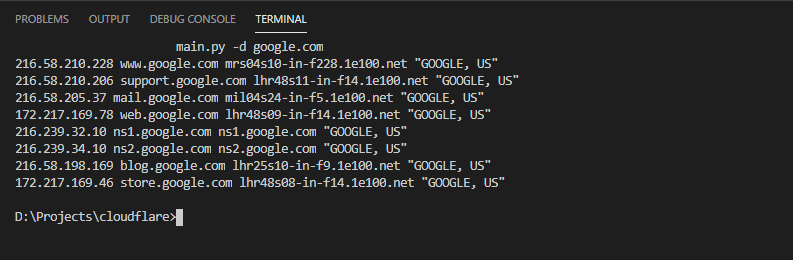
$ main.py -d google.com
216.58.210.228 www.google.com mrs04s10-in-f228.1e100.net "GOOGLE, US"
216.58.210.206 support.google.com lhr48s11-in-f14.1e100.net "GOOGLE, US"
216.58.205.37 mail.google.com mil04s24-in-f5.1e100.net "GOOGLE, US"
172.217.169.78 web.google.com lhr48s09-in-f14.1e100.net "GOOGLE, US"
216.239.32.10 ns1.google.com ns1.google.com "GOOGLE, US"
216.239.34.10 ns2.google.com ns2.google.com "GOOGLE, US"
216.58.198.169 blog.google.com lhr25s10-in-f9.1e100.net "GOOGLE, US"
172.217.169.46 store.google.com lhr48s08-in-f14.1e100.net "GOOGLE, US"The results shown from the scan show the sub domain scanned, its IP, host-name, and ASN. If the domain is using an CDN, you can figure it out through the ASN name displayed for the IP. The first sub-domain ‘WWW’ is likely to be on the cloud network. Subsequent sub-domains scans will show if it doesn’t match the IP for previous subdomains. It may find multiple subdomains on different IP, you will have to figure out which one hosts the actual domain.
The script can get subdomains of a domain found by VirusTotal using its API. But it isn’t used for CDN reveal at the moment. I would like to implemented it some day. You can get the sub-domains with the vtd.py file.
$ vtd.py -d google.com
mw1.google.com
translate.google.com
search.google.com
takeout.google.com
news.google.com
sites.google.com
spreadsheets.google.com
messages.google.com
adservice.google.com
gg.google.com
clients1.google.com
fcmatch.google.com
apps.google.com
analytics.google.com
accounts.google.com
apis.google.com
clients2.google.com
cse.google.com
voice.google.com
myaccount.google.com
pack.google.com
store.google.com
policies.google.com
ogs.google.com
hangouts.google.com
fi.google.com
dl.google.com
maps.google.com
calendar.google.com
notifications.google.com
mail-settings.google.com
dns.google.com
groups.google.com
fonts.google.com
payments.google.com
clients4.google.com
surveys.google.com
trends.google.com
tagmanager.google.com
gsuite.google.comAfter you find the different IP used by the different sub-domains. Point the domain to the specific IP on the host file of your operating system. If the website loads without problems, you have found its real host IP.